We have got few new automation requests all are based on Microsoft Intune Product.
On doing bit of research we have found Intune module available on Git HUB as well as PowerShell gallery.
https://github.com/microsoft/Intune-PowerShell-SDK
https://www.powershellgallery.com/packages/Microsoft.Graph.Intune
To install it from PowerShell Gallery use the command Install-Module -Name Microsoft.Graph.Intune
Ones you have installed it, first time you need to use
Connect-MSGraph -AdminConsent
This will ask for permissions same as any other Graph/Rest application when you connect to office 365 (I have used my Global admin account for first time installation/Configuration)

What this does is create Application Name : Microsoft Intune PowerShell under Enterprise applications in Azure AD.
After first time if admin consent has been granted successfully you only have to use Connect-MSGraph
Note: Any user in the organization will be able to connect it and that made me bit nervous but when I have tested with different test ids to connect it , they all got connected but they all were throwing
RED errors of unauthorized until I have granted them Intune Administrator rights, that has given me a sigh of relief.

I still do not want any one to be able to connect to it and I follow one of the practice called user assignment for Applications which is disabled by default.
Go to the application under AZURE AD, hit properties and say yes to User Assignment required, I also set visible to user to NO for these type of applications.

Ones that is done, go to users and groups under this application. assign the users that you want to allow connection to this APP.
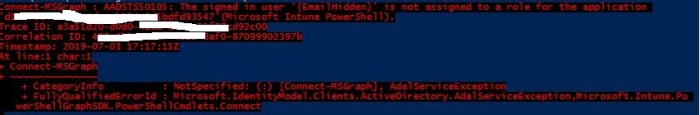
Any other user, if he or she will try to connect will get the below error: (is not assigned to a role for the application)
Now you will be able to run the commands such as getting all managed devices : Get-IntuneManagedDevice

Enjoy and automate Microsoft Intune with this PowerShell module, do not forget about user assignment if you want to control who can use it.
Thanks for reading
Sukhija Vikas
Thank you very much for posting this. This is the clearest explanation that I have found on how to add the Microsoft Intune PowerShell app to Enterprise Applications if it is not already present.
Pingback: Intune Marking devices as Corporate |
Pingback: Intune – Export MAM Devices Report | Tech Wizard
Pingback: Intune – MDM Enrollment Welcome Email | Tech Wizard
Pingback: Intune Duplicate Device Cleanup | Tech Wizard
Pingback: Intune Cleanup Not Evaluated Devices | Tech Wizard
Pingback: Intune Bulk Device Removal Tool | Tech Wizard
Pingback: Intune A Granel Dispositivo Herramienta De Eliminación De - Actual Tecnología
Pingback: Intune – Check Particular APP installation on Devices | Tech Wizard
Pingback: Use PowerShell to report on Intune devices – Savage Nomads
Do the the Intune permission scopes on the app work well with Inrune RBAC (roles defined via scope tags)? Do the app permissions take precedence or does your account also need specific Intune roles?
Account needs to have intune role else it will get connected but will get unauthorized on executing commands as tested and stated in the article..
Thanks. I asked about the RBAC because the article mentioned the Intune administrator role. Performed a quick test with an account that has access to a limited set of devices and the api did stay within that scope.
Hi Sukhija,
I am not able to download this tool – Intune Bulk Device Removal Tool | Tech Wizard
can you please make it available again?
Regards,
Ravikant
Its available, I checked and able to download it.